Public key cryptography is widely used by banks to perform secure money transfers, or over the internet for securing website access. The security of public key cryptography relies on the difficulty of realising an efficient algorithm to “crack” the communication. These protocols are not, however, unconditionally secure because no mathematical theorem forbids an eavesdropper (Eve) from building a clever algorithm, or a quantum computer, that will allow her to crack such codes.
On the other hand, private key cryptography can be unconditionally secure if encryption techniques such as the ‘one time pad’ are performed. The weakness of these techniques is that the key has to be securely transmitted by Alice to Bob. This can be done by using a courier, a plane ticket and a briefcase, but one then depends on the courier being honest.
Quantum cryptography elegantly solves this problem by enabling the unconditionally secure transmission of a random binary key between Alice and Bob, and hence is very often referenced as Quantum Key Distribution (QKD). Basically, the security of the transmission is ensured by the no-cloning theorem that forbids the perfect reproduction, or cloning, of a quantum system without disturbing it, therefore enabling Alice and Bob to detect the presence of a potential eavesdropper.
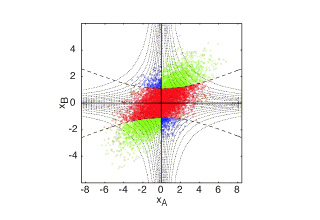
Data shared between Alice and Bob in a continuous variable QKD protocol. (publication).
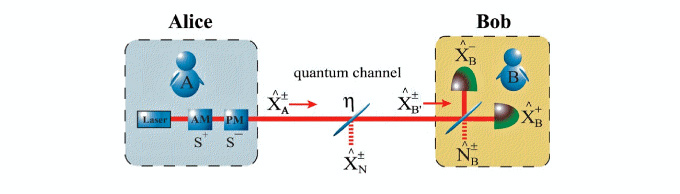
Bennett and Brassard proposed in 1984 and demonstrated in 1992 the first discrete variable (DV) quantum cryptography protocol known as BB84. DV-QKD is still the subject of successful ongoing, however, new approaches are being considered in order to make quantum cryptography feasible with bright light sources. The later are known as Continuous Variable (CV) and are motivated by the availability of efficient detectors, and the maturity of bright light sources compatible with the present optical communication systems operating at very high rates.
The main goal of this program is to demonstrate Quantum Cryptography in the Australian Parliamentary Triangle. In close partnership with QuintessenceLabs, The University of Queensland and Lockheed Martin Australia,we will implement the Government Quantum Network (GQN). This is an initiative of multiple governmental agencies to provide the highest level of information security for intra-governmental communications in Canberra. In order to achieve this goal, the secure quantum communication program is developing a post-selection based continuous variables quantum key distribution device. We concentrate on all the aspects of such a device, from the physical optical implementation, theoretical modelling, and underlying analogue and digital electronics, to the information processing algorithm and integration into existing telecommunication networks. In parallel with the first field trial in Australia, we will develop industrial standards in tandem with the European Telecommunications Standard Institute and the Australian Department of Defence.